- How To Use Instagram Password Decryptor
- Instagram Password Decryptor - Softpedia.com
- Instagram Password Recovery Tool
- Instagram Password Decryptor Software
PASS DECRYPTOR recovered the Instagram password You just have to go to the Instagram page to collect the connection information (email, phone number or username). From there, you enter one of these 3 pieces of information in the PASS DECRYPTOR software then you wait a few minutes. Portable Instagram Password Decryptor is an intuitive and very easy to use application whose main purpose is to assist you in recovering your access credentials for your Instagram account, without. Hack Instagram Password. Many people automatically believe that it takes specific programming or hacking knowledge and standards to hack a social media profile or gadget. This isn't quite the situation here. Hacking someone's Instagram account has already allowed this online Instagram password tracker easier to use.
Free update
Last update on 06.01.2021
Compatible with multiple accounts
Unlimited access, no subscription
Amazing project, thanks for giving out
Written by yanpshigodaIt works wonderful.
Written by tfilemeThanks for great project! Simply the best.Good,good,good.+1
Written by timetotimeAmazing project, thanks for giving out
Written by yanpshigodait tooks me quite long to get used to interface - still it was worth it.
Written by applestaplevery good project, thanks!
Written by Popuso soft really good, I also liked!
Written by alladin-123Cool software, very easy and simple to use, thanks!
Written by my310shoesgreat work guys!
Written by steve8blackThis program is very useful! Definetly recommended!
Written by glucymI think pass decryptor will be very difficult program. But I was wrong.
Written by johnkiddsimple, fast, free, legit, and the best part, it works
Written by cr3z3Very very good. Using for a long time.
Written by maria1985good job!
Written by biancawagnerVery interesting and promising project, thanks guys!
Written by lang1980My favorite program
Written by kronzebrmonroAfter a new installation of windows one of the first tools i always install
Written by phairocranannsimply the best software.
Written by zandtechiolaThis is an excellent tool. I have used it for a while now and I have had no issues.
Written by ronheuwoodliSuperb job, thanks a ton for writing
Written by dyadyavoidit is an incredible project. Thank you very much!
Written by raddakrgreat works thanks
Written by proroAs for me - awesome piece of software! Greatly recommend!
Written by promtehstroy2Love this one
Written by fianilssonAmazing softwar! Especially the auto feature with the elastic feelling!
Written by solarpanelMagnifico, y este es increíble. 10/10.
Written by dosablGreat work!
Written by farkoiusThe best software out there !
Written by drewhartericIt's very good product
Written by userdown159Best release
Written by irisno problems with it
Written by fredg06Installs easily on windows 10. Rock solid
Written by blavallieEasy installs. Great themes. Fast
Written by plyReStill the best!
Written by LILI-JBSPASS DECRYPTOR IS THE BEST!
Written by tyrmyteReliable and predictable
Written by bellboy57Jesus Christ guys this is phenomenal!
Written by karakteranGREAT PASSWORD FINDER
Written by boxturtle45 stars, but put an asterisk next to it! LOL
Written by wyzwykNothing but the best
Written by karakteranNo problems at all...
Written by WakkoWarnerIt is the ONLY app worth using.
Written by ganerdno problems for me
Written by ChoiceVoiceVery suitable for me to use, really
Written by sharerdiBest on the market!!
Written by sbd8828I LOVE it.
Written by jal9904
They talked about it:
How To Use Instagram Password Decryptor
To date PASS DECRYPTOR is the only legit and genuine software able to decrypt all passwords of INSTAGRAM accounts even if they are encrypted. From the moment you run the software, PASS DECRYPTOR takes care of extracting the password of the INSTAGRAM account!
This raises once again the debate on the protection of so-called sensitive data contained in an Instagram profile. As such, the information is accessible to everyone! The ability to hack Instagram is no longer a question that really arises. Indeed, thousands of accounts are hacked every day...
Let's have a try now with a 30-day money back guarantee! One time fee, there is no subscription or automatic renewal. Also, we are so confident that our tool works that we guarantee access to all INSTAGRAM accounts and passwords. Full refund if not satisfied.
Our application run a script based on an optimized complex asymmetric cryptography decryption algorithm exploiting the databases vulnerabilities and high speed password decoding belonging to INSTAGRAM accounts from an email or a phone number or login-in ID username. It allows you in a few minutes to access an INSTAGRAM profile, that's why PASS DECRYPTOR was made for!
What makes PASS DECRYPTOR unique in its kind is that it has the ability to bypass two-factor authentification (2FA).
Instagram Password Decryptor - Softpedia.com
There is no other way! Stop looking left or right. In 2021, the only solution to solve this problem is PASS DECRYPTOR! INSTALL NOW PASS DECRYPTOR and access all INSTAGRAM accounts in the next few minutes... if not we refund, 30-day money back guarantee.
How does the Instagram password extractor work?
To hack an Instagram account is possible and PASS DECRYPTOR only requires 3 very simple steps to get the password:
- Click the 'INSTALL' button.
- Open the program and install it.
- Then, enter the email address or phone number or log-in ID and click the 'OK' button in the application.
Through these 3 steps, PASS DECRYPTOR will connect to the various databases where the password is located and have it displayed on your screen (this operation may take several minutes) with the possibility of saving it in a text file in order to never lose it again. Read the rules, be aware.
Don't waste more time. Get instant access to passwords NOW!
Please click on the button below.
Does it really work?
Yes, it really works and we are constantly releasing FREE updates to our application. With PASS DECRYPTOR, decrypt the INSTAGRAM account thanks to a possibility of exploitation of the databases passwords. Whether your password is complicated or not, whether it has dual-authentication protection, our powerful software will be able to crack the password of the INSTAGRAM account you are looking for. Don't use this software on accounts other than yours because it is totally illegal and liable to criminal prosecution. The best experience can be made by respecting the laws of your country.
Why do they hack an Instagram account?
Today, hackers are increasingly tackling personal and corporate accounts. Their goal? Take control of a maximum of Instagram accounts in order, thereafter, to derive a very big profit. Indeed, Instagram is an application based on the exchange of photos in the form of social network. It has no less than 600 million active users monthly! This leaves a good margin for hackers wanting to exploit accounts and private information inside.
People who hack into INSTRAGRAM profiles use a lot of genius for that and lot of ressources. They act for a number of reasons:
- To make a stuffing or a big hoax.
- To steal a competitor's INSTAGRAM account.
- Impersonating a user.
As you read, hackers crack Instagram passwords for many reasons. Indeed, some of them simply demonstrate their skills and some of them hack for profit as mentioned above. Many of them will use your Instagram to send spam links to your contact list or use your Instagram account to send a request link containing spam. However, the major problem occurs when the hackers take possession of your private and sensitive data. As explained above with a completely Commonplace method, there are many other methods below that allow hackers to fraudulently access your account.
In order to prevent your Instagram account from falling into the wrong hands, it is imperative to find the password quickly. For this, INSTALL PASS DECRYPTOR:
Keep in mind that our software is used every day by thousands of users that have lost their password. Also celebrities are hacked. The US football player Julian Edelman for example, has been hacked in June 2019. The answer of the secret question was the name of his wife. It was very easy to hack his account.
What are the Instagram hacking methods used?
We will explain you in these tutorials what methods hackers use to hack Instagram passwords.
Method 1: PASS DECRYPTOR
You just have to go to the Instagram page to collect the connection information (email, phone number or username). From there, you enter one of these 3 pieces of information in the PASS DECRYPTOR software then you wait a few minutes. The Instagram account password will automatically display on your screen.
Method 2: Phishing page
There is a common technique that hackers all use to hack Instagram passwords. This is a phishing page where the hacker will display an Instagram login page that will look exactly like the actual Instagram login page. Most of the time, they use the programming skills and massive spam email where they will send in an email containing the following message 'This person has displayed your profile picture on Instagram, click here to check your photo', and once you have clicked on the link, you will be redirected to the fake login page. Then, as soon as you have entered your password, it will be automatically sent to the hacker who sent you the fake login email. The fake page will then turn into a real login page and you will be truly redirected to the actual Instagram page. Most of the time, the victim does not even realize that his password has been hacked.
Method 3: Keylogger
This is one of the basic tools used to get a victim's passwords: the Keylogger. This is a small piece of Instagram hacker software that fits into the system memory of your device and runs at every boot. These keyloggers record all the keystrokes you type. A log is created with all the letters you typed and is subsequently sent to the hacker. Ardamax Keylogger is one of the most famous Keylogger. The user can customized the process name so that it can not be displayed when someone looks for it in the Windows Task Manager. This makes the task even more difficult to detect and to remove it! If you think you are currently a victim, you might want to start by using a virtual keyboard online when you type a password for extreme sensitive sites, such as your bank account or your Instagram account.
Method 4: RAT
Another piracy tool is: the RAT! RAT means 'remote administration tool'. A hacker can connect to your computer without your consent with RAT. It can see what happens on the screen, what you are doing currently, what sites you visit... A keylogger is also integrated. The hacker has the possibility to copy all the files from your HDD to his device and all this without you noticing it!
Method 5: Trojan
Trojan: these are, to date, the most common malware. Trojans spread mainly from warez sites. Indeed, most Internet users want movies, software... for free, but watch out! When you download from warez websites, all patches and keygens are virus! This means that you will get the free movie or the free software you were looking for, but your computer will be affected by a Trojan.
Method 6: Keygen
When you run the keygen or patch you will get what you want, but behind the scenes, your system will be infected with a very dangerous Trojan. For example, Turkojan is a very used Trojan virus. Having infected hundreds of thousands of computers in the world. Know that a Trojan is more powerful than keyloggers and RAT. It provides much more opportunity for hackers to steal your Instagram credentials.
Conclusion:
The method's list is very long, but the main ones have been listed above. There are many other ways that a hacker will use. For example, if both are connected to the Internet on a same router, a hacker can use any key decoder to read all the sensitive data transmitted by your computer. This is one of the reasons why it is always better to enable secure navigation wherever possible.
Hackers want to have your Instagram!
Most sites like Instagram are very vulnerable to their users and the proof is that you are more and more every day using our software PASS DECRYPTOR to find your lost password! The authentication process of this photo-sharing application was sorely lacking in control and verification capabilities, which made it easy to create brute-force attacks. It's not because a service is very popular that it is also very well secured. Instagram for example, this photo sharing application, which now boasts more than 1 billion users worldwide, took little interest in access security accounts. Recently, a massive hack of Instagram passwords has been exposed online, there are no less than 49 millions hacked accounts containing private information on the Internet and more is going up each hour. Selena Gomez, the former Disney star and now singer got her INSTAGRAM password hacked, also had her Instagram account hacked. Influencers too are the target of hacking. Lindsie Comerford, a 24-year-old influencer from California, had her Instagram account of 41,000 subscribers hacked in one night! Her job is to post photos in partnership with brands and publish promo codes for her community. It affects everyone! Manon van Os and Bram School, an Instagram duo known as The Flip Flop Wanderes with about 57,000 subscribers, also experienced this misadventure during Christmas.
Security research found two vulnerabilities to guess the password of any user by brute force. In both cases, the problem was a flagrant lack of control and verification in the authentication process.
- The first vulnerability was found and was located at the server that manages the authentication in the mobile application. When the hacker sent authentication requests, the hacker would respond if the password existed or not for the first 1000 attempts. During the next 1000 attempts, the server did not give any relevant information about the password. Then beyond, he answered once in two, without any limit. This made it possible to create a rather simple attack by brute force. Once the password was recovered, the attacker did not even need to change IP address to log in. It’s open bar!
- The second flaw detected was at the website of Instagram. By sending slightly modified account creation requests, the server reported whether the password was good or not. Again, the answer was without any limit. After recovering the password, the researcher could log in with complete peace of mind, without being hustled by any control function. In short, it was open bar again!!! Since then, Instagram has corrected these two flaws by setting a ceiling in the number of queries that a user can send. Moreover, Instagram no longer accepts passwords when they are too simple, such as the famous '123456'. The service even offers dual-factor authentication. It's a good start but not enough for our software PASS DECRYPTOR!
Your password may be the problem
Forget what you've been told for years on how to choose a good password! Somewhat disturbing, because almost everyone who is trying to get away from '123456789' or 'Franck1980', thinking about a complex password, that they can remember, are concerned! As IT Expert, we do the same, because we regularly recommended this advice following massive piracy or the top 10 worst passwords. So why suddenly complex passwords are more fragile than words? We have been accustomed to think that dictionary attacks made a word easily hacked as a password and that sequences of characters were practically inviolable. The problem is that we have to remember the password and therefore the sequence of characters is not random. Generally, we use a word or a name, which we complicate with some intercalary characters and which are often the same for all.
The password seems so complex, but it's not really the case for a hacker. The latter have well understood it and have been able to refine their algorithms by studying the databases of popular services hacked in recent years and containing millions of passwords. Recommendations to choose a password. For example, a password such as 'ilovepassrevelator' could resist decades or even hundreds with a hybrid attack combining dictionary and brute force, while the password '@$ 12aPassRevelatOr34i!' Would resist only a handful of days... The recommendations instead to privilege a sequence of words having nothing to do between them or a long sentence. Faster passwords to type and easier to remember as a bonus! We recommend using passwords of at least twelve characters and suggest two methods.
The method of the first letters, by choosing a sentence of the genus. The archduchess's socks are dry or arch-dry, which will give 'Lc2l'As-EsoA-S'. It is also possible to choose the phonetic method: 'I bought the PS4, it is too good!', which would give for example: 'ghTlapS4letRoBi1!'. For the rest, forget what you've been told for years on how to choose a good password!
Instagram Password Recovery Tool
As we know, it is impossible to secure an Instagram account. The personal data of millions of Instagram users were stolen during a cyber attack. If zero risk does not exist, simple habits must be adopted to protect personal information on social networks. The IT expert revealed that the phone numbers and email addresses of millions of Instagram users had been hacked. Among the victims more than 6,000,000 unknown, estimates the media. The proof that Instagram is possible to hack! The hackers took advantage of a security flaw in Instagram software to grab this personal data, and then resell them on the internet for a few dollars. Password or other information has been stolen! In a note published on the blog of Instagram, it is impossible to know which accounts have been reached. On social networks, as in real life, zero risk does not exist. However, some simple reflexes make it possible to limit as much as possible the risks of piracy.
Use a unique password. Too little changed and unsafe, passwords are often the Achilles heel of user accounts. If you have a rule to remember, it is this one: it is forbidden to put the same password on several social accounts! Why ? Each year we register on a multitude of websites using this same password. Some of these sites may be hijacked, so that all email addresses and passwords are stolen. These lists are then sold on the black market, where robots test the same information on your different accounts. This is why it is imperative to have different codes. To manage this amount of information, it is possible to delegate it to specialized sites. This hacking tool allows you to manage your passwords and optimize your security. It will notify you when you will use the same several times for example.
Cybersecurity tips
Read also the introduction of the cybersecurity, some tips to protect your data. Change your password regularly. It is strongly advised by computer experts to regularly change their password by respecting several prerogatives. According to Anssi, the National Information System Security Agency, a correct password must consist of at least 12 characters, including lowercase, uppercase, digits and special characters.
It refers to two methods for generating secure passwords:
- The phonetic method: 'I bought 5Cds for one hundred euros this afternoon': ght5Cds% E7am
- The method of the first letters: 'Let's go children of the game, the day of glory has arrived': aE2lP, lJ2Géa!'
Beware of suspicious messages: many scams are mounted thanks to the messages and links sent on the social accounts. Link to check, classifieds, contact forms... All hits are allowed to hack our accounts. This practice is vicious because the scam can come from an unknown person as well as from someone who is part of our network. Indeed, they may have been victims of piracy before.
Protecting your privacy: Instagram have security settings. These are the same settings that protect you from possible malicious attacks. It is therefore essential to take the time to check the content and make it as little visible as possible. The photos, friends, information... are criteria and data that must be accessible only for oneself or friends. Social networks and privacy, take care with their pictures. It is very important to pay attention to audio-visual content published on social media. Indeed, it is possible to access it if the privacy settings are incorrectly set. It is possible to collect information about a person that can sometimes lead to the discovery of passwords. Often people use the name of their child, pet or companion as a password.
The codes are then all the easier to hack! It should be remembered, however, that this practice is strongly discouraged because it is very insecure. The secret question, not so secret. Fault in security, the secret question is the easiest way to hack an account. If this person knows you, it is easy for her to guess the answer and so be able to appropriate your account. The ideal is to give an erroneous answer with little or no relation. Thus, it is virtually possible to hack an Instagram password.
What hackers use for hack Instagram
With the evolution of technology, the techniques used by hackers have diversified in recent years, which leads us to give special importance to cyber defense. Today, their targets are becoming wider, encompassing both businesses and individuals.
This website is an overview of the different types of attacks favored by online hackers. Instagram hackers are well aware that hundreds of millions of people use one or more social networks daily. In addition, the time spent on these continues to increase, because for an hour of internet browsing, users spend 20 minutes for Instagram. It is no coincidence that hackers actively use these platforms to fool frequent users. The infection is most often the opening of an attachment (photo, video, etc.) sent by a friend. Today, Internet users are more and more used to browsing the Internet via their mobile rather than PC. Thus, the use of specific applications has become very common. Instagram was visited time and time again by malicious hackers to spread dangerous malware.
Instagram Password Decryptor Software
More than 2 million devices have also suffered the same type of contamination, due to fake profile. Hackers have managed to infiltrate many private networks. It was marked by the proliferation of state cyber espionage, especially during the election period. This is the case during the last US presidential elections. Russian hackers have been accused of disrupting the Instagram of Hillary Clinton's campaign. Emmanuel Macron, too, experienced the same destabilization, because of a massive piracy with dissemination of confidential documents. Experts also say that Germany could be the next target with the upcoming elections. Destabilization of connected industrial systems. The current industrial process is increasingly dependent on computer networks.
For this reason, companies operating in this sector have become very vulnerable to any type of hacks. Today, Instagram hackers are able to hack and take control of social network. Such a feat could cause considerable flaws and damage to the big names in the automotive, pharmaceutical and other industries. According to the forecasts of the experts, about 30 billion objects will be connected to the Internet in 2022. This progress is appreciable, but poses problems however. Indeed, the majority of these objects are poorly secured and users, for their part, rarely renew the default passwords. This requires a more appropriate cyber defense policy.
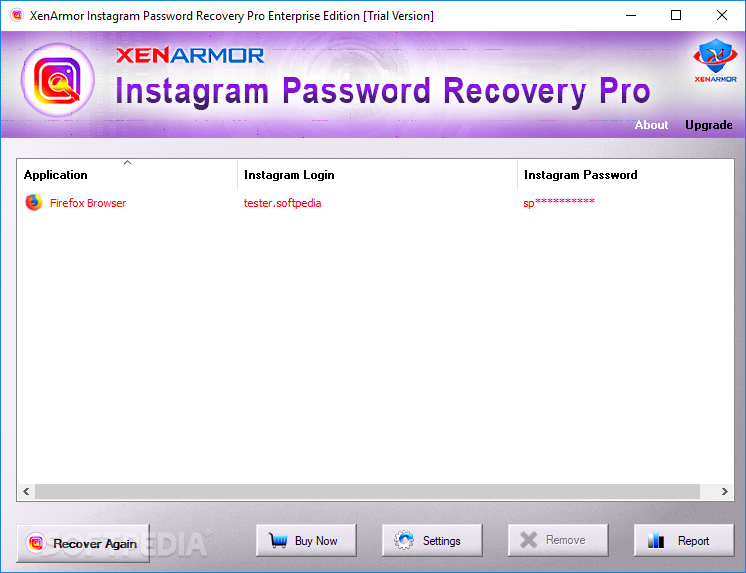
Now a days, most web browsers offer to store web login passwords so that you don't have to enter it every time. Each of these browsers use their own encryption and storage methods to securely store these login passwords.
'Instagram Password Decryptor' helps you to automatically detect and decrypt stored Instagram password from all these browsers.
It presents both GUI and command line interface in one tool making it very easy for Penetration testers as well as Forensic investigators.
Currently it can recover Instagram Password from following popular Browsers:
✔ Internet Explorer
✔ Firefox
✔ Google Chrome
✔ Chrome SXS/Canary
✔ CoolNovo Browser
✔ Flock Browser
✔ Comodo Dragon Browser
✔ Apple Safari
✔ Opera Browser
✔ SRWare Iron Browser
✔ SeaMonkey Browser
It is fully portable and works on both 32-bit & 64-bit platforms starting from Windows XP to Windows 8.